In this article I'll share a step by step of how to add ssh authentication to a private Github repository:
Create the key pair (select empty passphrases on prompt)
ssh-keygen -t ed25519 -C "mateo.cuervo@example.com" -f ~/.ssh/argocd_ed25519
Copy the public key
cat ~/.ssh/argocd_ed25519.pubGo to your Github repo, you should be admin, then click on "Settings" then on "Deploy keys" and finally save the key copied in last step.
Now copy the private key part
cat ~/.ssh/argocd_ed25519
Create a kubernetes secret with the key final result should look something like this:
apiVersion: v1
kind: Secret
metadata:
name: repo-secret
namespace: argocd
labels:
# This annotation let's ArgoCD know it's for repository authentication
argocd.argoproj.io/secret-type: repository
stringData:
url: git@github.com:cooervo/my-repo-name.git
sshPrivateKey: |
-----BEGIN OPENSSH PRIVATE KEY-----
...
-----END OPENSSH PRIVATE KEY-----
insecure: "false"To automate above step, you can use pulumi secrets to encrypt your secret and then programatically deploy it into your cluster. First read from source and pipe it into a pulumi secret.
# Read the private SSH key from the file
cat ~/.ssh/argocd_ed25519 | \
# Set the SSH key as a Pulumi secret in the config
pulumi config set \
--path my-path:dev-core.argoCdSShPrivateKey \ # Specify the configuration path
--secret \ # Mark it as a secret
-s dev-core # Specify the stack (dev-core)Alternatively, you can also do use the secret directly in instead of piping from a file
pulumi config set \
--path my-infra:my-stack.secrets.argoCdSShPrivateKey --secret '
-----BEGIN OPENSSH PRIVATE KEY-----
...
-----END OPENSSH PRIVATE KEY-----'You can then create the k8s secret and deploy it in your cluster when running pulumi update
const sshKeyForArgoCd = new k8s.core.v1.Secret(
`${env}-ssh-argocd-github-infra-repo-private-key`,
{
metadata: {
namespace: 'argocd', //should be in same ns as argocd-server
labels: {
// This label lets ArgoCD know it's for repository authentication
"argocd.argoproj.io/secret-type": "repository",
},
},
stringData: {
url: "git@github.com:my-org/my-repo.git",
// sshPrivateKey is the value from pulumi config secret at
// argoCdSShPrivateKey which is encrypted with GCP KMS
sshPrivateKey: config.secrets.argoCdSShPrivateKey,
},
},
{ provider: k8sProvider }
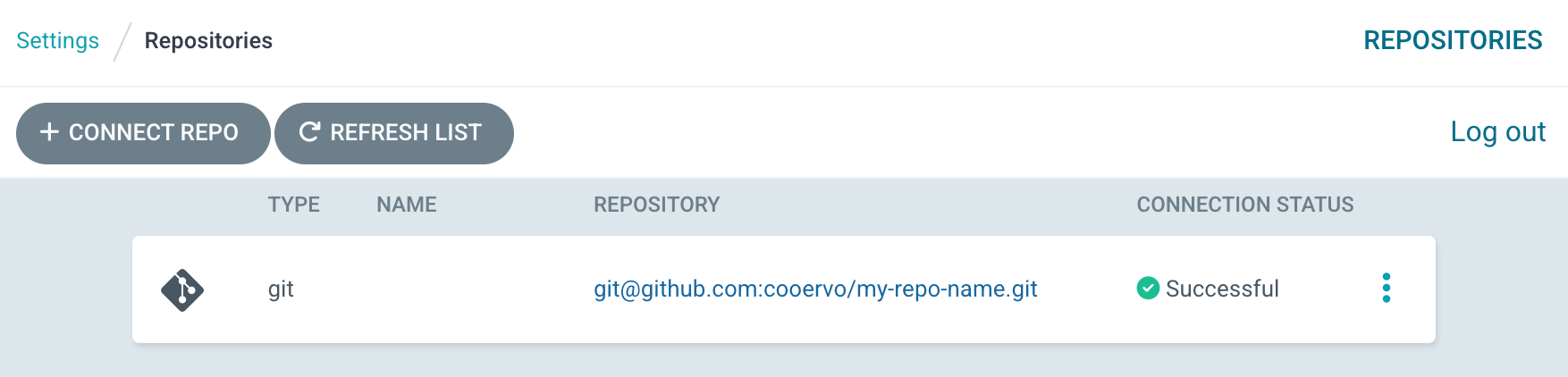
);Next open your ArgoCD server UI navigate to "Settings" > "Repository", your repo should be connected: